Mobile Connect Federated Authenticator for WSO2 Identity Server
- Keet Malin Sugathadasa
- Oct 3, 2016
- 5 min read

The Mobile Connect Authenticator allows you to authenticate users using Mobile Connect through the WSO2 Identity Server. Follow the configuration steps given below to set up the Mobile Connect Federated Authenticator in the WSO2 Identity Server.
To view more connectors supported by the WSO2 Identity Server, visit this link.
Getting Started
To get a better understanding on what Mobile Connect and WSO2 identity Server are, please refer the below links.
Watch the Webinar done by WSO2.
This page provides instructions on how to configure the Mobile Connect Authenticator and the WSO2 Identity Server using a sample app to demonstrate the authentication process.
1) Deploying the Mobile Connect Authenticator
You can use either "METHOD 1" or "METHOD 2" for this purpose.
METHOD 1 (Download from the store)
1.1 Download the WSO2 Identity Server from here.
and Extract it and that folder will be referred to as <IS_HOME> in future.
1.2 The authenticator and the artifacts mentioned below can be downloaded from the store for this authenticator.
1.3 Copy the above .jar file (org.wso2.carbon.extension.identity.authenticator.mobileconnect.connector-1.0.0.jar) into "<IS_HOME>/repository/components/dropins" directory.
1.4 Copy the .war file (mobileconnectauthenticationendpoint.war) into "<IS_HOME>/repository/deployment/server/webapps" directory. (It can be located inside "other_artifacats.zip" archive downloaded from the store)
METHOD 2 (Build from the code)
1.1 Download or clone the code from github using the link: https://github.com/wso2-extensions/identity-outbound-auth-oidc-mobileconnect
1.2 Build the code (using "mvn clean install").
1.3 Download the WSO2 Identity Server from here.
and Extract it and that folder will be referred to as <IS_HOME> in future.
1.4 Locate the org.wso2.carbon.extension.identity.authenticator.mobileconnect.connector-1.0.0-SNAPSHOT.jar file in "identity-outbound-auth-oidc-mobileconnect/component/authenticator/target/" directory.
1.5 Copy the above .jar file into "<IS_HOME>/repository/components/dropins" directory.
1.6 Locate the mobileconnectauthenticationendpoint.war file in "identity-outbound-auth-oidc-mobileconnect/component/authentication-endpoint/target/" directory.
1.7 Copy the .war file into "<IS_HOME>/repository/deployment/server/webapps" directory.
2) Configuring Mobile Connect Authenticator Parameters
2.1 Navigate to "<IS_HOME>/repository/conf/identity" and open the "application-authentication.xml" file.
2.2 Inside the "<AuthenticatorConfigs>" tag, insert the following code segment.

<AuthenticatorConfig name="MobileConnectAuthenticator" enabled="true"> <Parameter name="MCAuthenticationEndpointURL">mobileconnectauthenticationendpoint/mobileconnect.jsp</Parameter> <Parameter name="MobileConnectKey">MobileConnectKey</Parameter> <Parameter name="MobileConnectSecret">MobileConnectSecret</Parameter>
</AuthenticatorConfig>
Replace the "MobileConnectKey" and "MobileConnectSecret" with the correct key/ secret values.
To know more details in depth on how to obtain the credentials for "MobileConnectKey" and "MobileConnectSecret" read this blog. Or simply you can follow the below steps.
You can always use Sandbox credentials provided by the "Official Mobile Connect Site." For this, do the following steps.
2.1 Navigate to https://developer.mobileconnect.io/#overlay=user/register and register by entering your name and email

2.2 Go to your email inbox, and click on the one time link received, to confirm your registration

2.3 Go to "My Account" Dashboard

2.4 Click on "My Apps"

2.5 On "My Apps" page, click "Add Application"

2.6 Complete the "Create Application" form with the following details and click "Create":
Name: Travelocity (any name you prefer)
URL: localhost:8080/travelocity.com/index.jsp (Any URL that will describe your application)
Description: "This is a test application" (Any description that will explain about the application)
Redirect URI: https://localhost:9443/commonauth (Use this URI)

2.7 You will see the confirmation message and your new app will be available in My Apps page now:

You can edit, delete or promote your application on the My Apps page .
When you create an application, the Developer Portal will generate the application key and secret for the Discovery API both on the Sandbox and API Exchange. You will get access to the Sandbox to test your application once you have integrated the Discovery API and the Mobile Connect APIs into your application. You can find these details on your application page under “My Apps” section, once the application has been successfully created.
2.8 Go to "My Account" and click on "My Test Numbers." Add the test numbers and click "Update"

2.9 Go to "My Account" and click on "My Operators"
Select the checkbox "Accept Terms and Conditions for all operators" and click on "Accept"

If you wish to obtain Official Mobile Connect Credentials (Production Credentials), read this blog, and go to section "Get Credentials for Production Environment" section. (With the sandbox credentials, you will most probably not be able to get the authorization request to your own mobile phone; for this use the production credentials)
3) Deploying travelocity.com sample app
The next step is to deploy the travelocity.com sample app in order to use it in this scenario.
3.1 You can download travelocity.com.war file from here.
3.2 Deploy this sample web app on a web container.
Use the Apache Tomcat server to do this.
Since this sample is written based on Servlet 3.0, it needs to be deployed on Tomcat 7.x.
Copy the .war file into the webapps folder.
For example, "<TOMCAT_HOME>/apache-tomcat-<version>/webapps".
3.3 To check the sample application, navigate to
http://<TOMCAT_HOST>:<TOMCAT_PORT>/travelocity.com/index.jsp on your browser.
For example, http://localhost:8080/travelocity.com/index.jsp
4) Configuring the identity provider
Now you have to configure WSO2 Identity Server by adding a new identity provider.
4.1 Run the WSO2 Identity Server according to these instructions.
4.2 Log in to the Management Console as an administrator.
username : admin
password : admin
4.3 In the Identity Providers section under the Main tab of the management console, click Add.

4.4 Fill in the required details as given below and click "Register"

Identity Provider Name: Mobile Connect (any name you prefer)
Display Name: Mobile Connect (any name you prefer)
Alias: https://localhost:9443/oauth2/token
Go to "Federated Authenticators" --> Mobile Connect Configuration
Enable : TRUE (check the checkbox)
Mobile Connect Authentication Type (Select one) - default "on-net"
(off-net : The Identity Server will always prompt a UI requesting for the users mobile number and carries out the authentication process)
(on-net : The mobile connect servers will identify the internet connection being used and identifies the MNO automatically. If it fails to identify, mobile connect will prompt one of their UIs, and will get the necessary details)
(If you have entered the relevant "Mobile Connect Key" and "Mobile Connect Secret" according to section 2.2 in this blog, you can leave the "Mobile Connect Key" and the "Mobile Connect Secret" fields empty. Else do the following)
Mobile Connect Key: xxxxxxxx-xxxx-xxxx-xxxx-xxxxxxxxxxxx (see below image: Key)
Mobile Connect Secret: xxxxxxxx-xxxx-xxxx-xxxx-xxxxxxxxxxxx (see below image: Secret)

Mobile Connect Scope: openid (mandatory value)
optional scope values are: “profile”, “email”, “address”, “phone” and “offline_access” (if you need to add more scope values, add each field with a space in between)
Eg: "openid profile email"
Mobile Connect ACR Values: 2 (Values accepted are 2 and 3)
These ACR values represent the Level of Assurance required when the authorization happens. If both values are required, add them with a space in between them (Eg: "2 3")
4.5 Click Register
You have now added the identity provider.
5) Configuring the service provider
The next step is to configure the service provider.
5.1 Return to the management console.
5.2 In the Service Providers section under the Main tab, click Add

5.3 Fill in the "Service Provider Name" as "Travelocity" (any name) and click "Register"

5.4 In the Inbound Authentication Configuration section, click Configure under the SAML2 Web SSO Configuration section.

5.5 Now set the configuration as follows
Issuer: travelocity.com
Assertion Consumer URLs: http://localhost:8080/travelocity.com/home.jsp (and click Add)
Select the following checkboxes
Enable Response Signing.
Enable Single Logout.
Enable Attribute Profile.
Include Attributes in the Response Always

5.6 Click "Register" to save the changes. Now you will be sent back to the Service Providers page. Go to the Local and Outbound Authentication Configuration section.
Select "Mobile Connect" from the dropdown list under Federated Authentication.
Ensure that the Federated Authentication radio button is selected and click Update to save the changes.

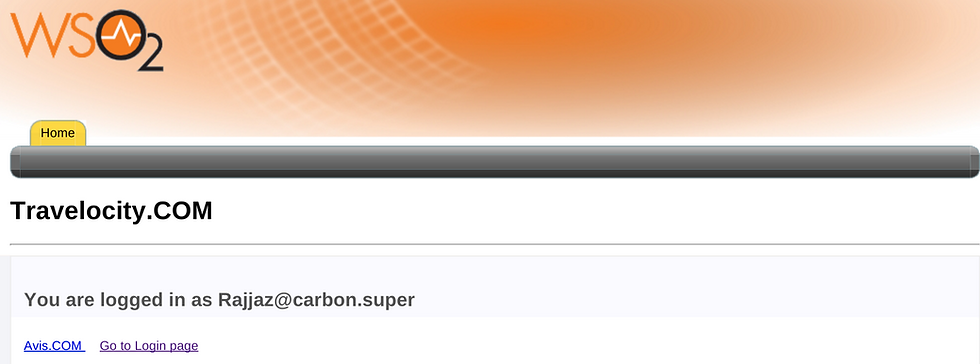
6) Testing the Sample (Travelocity App)

6.1 To test the sample, go to the following URL:
http://<TOMCAT_HOST>:<TOMCAT_PORT>/travelocity.com/index.jsp.
6.2 Click the link to log in with SAML from WSO2 Identity Server.
6.3 You are redirected to the Mobile Connect Authorization Page or the Mobile Number request page.

6.4 Once you confirm your identity via the mobile device, you are taken to the home page of the travelocity.com app
References:








Comments